What’s Cloning Software?
Okay, so imagine your computer as your entire digital life â all your photos, games, work files, and that perfectly curated Spotify playlist you’ve been building since middle school. Now imagine losing ALL of that in one crash. Sounds like a nightmare, right?
That’s where cloning software swoops in like a digital superhero. It’s basically like creating a perfect twin of your entire computer system, so if anything goes wrong, you can literally clone your way back to life. Whether you’re a college student protecting four years of projects, a content creator safeguarding your portfolio, or just someone who’s tired of starting from scratch every time technology decides to betray you â cloning software is about to become your new best friend.
What is Cloning Software?
Cloning software is a specialized type of program designed to create exact copies (clones) of computer hard drives, partitions, or entire systems. Think of it as a sophisticated photocopier for your digital storage devices. Unlike simple file copying, cloning software duplicates everything â the operating system, installed programs, system settings, hidden files, and even the exact structure of the storage device.
The process involves creating a sector-by-sector copy of the source drive to a destination drive, ensuring that every bit of data is perfectly replicated. This comprehensive duplication means that the cloned drive can immediately replace the original drive and boot up exactly as if nothing had changed.
How Cloning Software Works
The cloning process operates at the lowest level of data storage, reading data directly from the disk sectors rather than through the file system. This approach ensures that even system-critical files that are normally inaccessible during regular operation get copied successfully.
Modern cloning software typically works through these steps:
- Source Analysis: The software scans the source drive to understand its structure, partition layout, and data distribution
- Sector Reading: It reads data sector by sector from the source drive
- Data Transfer: The information is transferred to the destination drive in the exact same locations
- Verification: Many programs include verification steps to ensure data integrity
- Bootloader Configuration: The software ensures the cloned drive can boot properly
Types of Cloning Software
Free Cloning Software
Clonezilla Clonezilla stands as one of the most popular free disk cloning solutions available. This open-source software supports various file systems including NTFS, FAT32, ext2, ext3, and ext4. While it uses a command-line interface that might intimidate beginners, it offers powerful features typically found in premium software.
AOMEI Backupper Standard This free version provides basic disk cloning capabilities with a user-friendly graphical interface. It supports system clone, disk clone, and partition clone operations. The software works well for home users who need occasional cloning tasks without advanced features.
Macrium Reflect Free Macrium Reflect offers a free version that includes disk cloning alongside backup and recovery features. It provides an intuitive interface and reliable cloning performance, making it suitable for both beginners and intermediate users.
Paid Cloning Software
Acronis True Image Considered the gold standard in the industry, Acronis True Image offers comprehensive cloning and backup solutions. It includes advanced features like active disk cloning (cloning while using the computer), universal restore capabilities, and cloud backup integration.
EaseUS Todo Backup This commercial software provides professional-grade cloning features with excellent customer support. It offers system optimization tools, advanced scheduling options, and enterprise-level security features.
Norton Ghost (Discontinued but Legacy) While no longer actively developed, Norton Ghost was historically significant in the cloning software market and many of its concepts influence modern solutions.
Key Features to Look for in Cloning Software
Sector-by-Sector Cloning
This feature ensures complete data integrity by copying every sector of the source drive, including empty spaces and hidden areas. This method guarantees that the clone will be identical to the original in every way.
Intelligent Cloning
Smart cloning algorithms can optimize the process by only copying used sectors, significantly reducing cloning time and allowing cloning to smaller destination drives (as long as they can accommodate the actual data).
Live Cloning
The ability to clone a drive while the system is running eliminates downtime and allows for seamless transitions. This feature is particularly valuable for business environments where system availability is critical.
Multiple File System Support
Quality cloning software should support various file systems including NTFS, FAT32, exFAT, ext2/3/4, HFS+, and others to accommodate different operating systems and storage configurations.
Bootable Media Creation
The ability to create bootable recovery media ensures that you can perform cloning operations even when the primary operating system won’t start.
Compression and Encryption
Advanced cloning software offers data compression to save storage space and encryption capabilities to protect sensitive information during the cloning process.
Best Cloning Software for Different Needs

For Home Users
Macrium Reflect Home users benefit from Macrium Reflect’s balance of features and usability. The free version handles most home cloning needs, while the paid version adds advanced scheduling and differential imaging capabilities.
AOMEI Backupper With its straightforward interface and reliable performance, AOMEI Backupper serves home users well. The software includes helpful wizards that guide users through the cloning process step by step.
For Businesses
Acronis True Image for Business Enterprise environments require robust, scalable solutions. Acronis provides centralized management, network deployment capabilities, and comprehensive reporting features essential for business operations.
Symantec Ghost Solution Suite Designed for large-scale deployments, this enterprise solution offers network-based cloning, remote management, and integration with existing IT infrastructure.
For IT Professionals
Clonezilla IT professionals often prefer Clonezilla for its flexibility, scriptability, and support for advanced storage configurations. The software’s ability to work with various storage devices and network protocols makes it invaluable for professional use.
DriveImage XML This lightweight solution appeals to IT professionals who need quick, reliable cloning without unnecessary features. It offers good performance and minimal system resource usage.
System Requirements and Compatibility
Hardware Requirements
Most cloning software has modest hardware requirements, but performance benefits significantly from:
- RAM: Minimum 2GB, recommended 4GB or more for faster processing
- CPU: Any modern processor can handle cloning, but faster CPUs reduce processing time
- Storage: Sufficient space for both source and destination drives, plus temporary files
- USB Ports: For external drives and bootable media creation
Operating System Compatibility
Modern cloning software typically supports:
- Windows 11, 10, 8.1, 8, 7, and often legacy versions
- Various Linux distributions
- macOS support varies by software
- Some solutions offer cross-platform capabilities
Storage Device Support
Quality cloning software should work with:
- Traditional hard disk drives (HDDs)
- Solid-state drives (SSDs)
- NVMe drives
- External USB drives
- Network-attached storage (NAS)
- RAID configurations
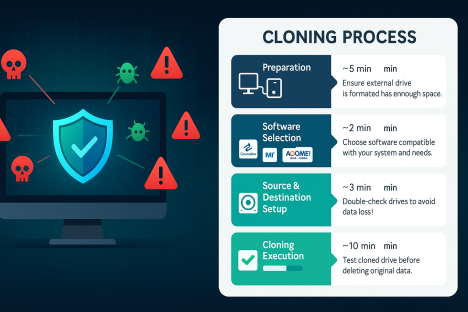
Step-by-Step Cloning Process
Preparation Phase
1. Data Assessment Before starting, evaluate what needs to be cloned. Determine if you need a full system clone or just specific partitions. Clean up unnecessary files to reduce cloning time and storage requirements.
2. Hardware Preparation Ensure you have adequate destination storage that matches or exceeds the source capacity. Connect all necessary cables and verify that both source and destination drives are properly recognized by the system.
3. Software Installation Download and install your chosen cloning software. Create bootable recovery media if supported, as this provides a backup method if the primary cloning attempt encounters issues.
Cloning Execution
1. Launch the Software Start the cloning application with administrator privileges to ensure access to system-level functions. Most modern software will automatically detect connected drives and display them in an intuitive interface.
2. Source Selection Choose the source drive or partition you want to clone. The software should display detailed information about the selected source, including capacity, file system, and current usage.
3. Destination Configuration Select the destination drive where the clone will be created. Verify that the destination has sufficient capacity and confirm that any existing data will be overwritten.
4. Cloning Options Configure cloning parameters such as:
- Verification settings to check data integrity
- Compression levels if supported
- Sector-by-sector vs. intelligent cloning
- Post-cloning actions (shutdown, restart, etc.)
5. Process Initiation Start the cloning process and monitor progress. Avoid using the computer heavily during cloning to prevent conflicts and ensure optimal performance.
Post-Cloning Verification
1. Integrity Check Most software includes verification features to confirm data integrity. Run these checks to ensure the clone was created successfully without errors.
2. Boot Testing If you cloned a system drive, test that the cloned drive can boot properly. This verification confirms that all system-critical files were copied correctly.
3. Functionality Testing Boot from the cloned drive and test critical applications to ensure everything works as expected. Check that all installed programs function normally and that user data is accessible.
Benefits of Using Cloning Software
Data Protection and Recovery
Cloning software provides comprehensive data protection by creating complete system backups. Unlike traditional file-based backups, clones include everything needed to restore a fully functional system, including the operating system, installed applications, system settings, and user data.
This comprehensive protection proves invaluable when facing:
- Hardware failures
- Virus attacks or malware infections
- System corruption
- Accidental file deletion
- Software conflicts that render the system unstable
System Migration and Upgrades
When upgrading to new hardware, cloning software eliminates the tedious process of reinstalling the operating system and all applications. The entire system can be transferred to new hardware with minimal downtime and configuration effort.
This capability is particularly valuable when:
- Upgrading from HDD to SSD for better performance
- Moving to a larger capacity drive
- Replacing aging hardware with newer systems
- Migrating between different computer models
Time and Cost Savings
Cloning software significantly reduces the time and cost associated with system restoration and migration. Instead of spending hours or days reinstalling software and reconfiguring settings, a cloned system can be restored in minutes to hours, depending on data volume.
The time savings become even more significant in business environments where:
- Employee productivity is directly tied to system availability
- Multiple systems need identical configurations
- Rapid deployment of standardized systems is required
- Minimizing downtime is critical for operations
Testing and Development
IT professionals and developers use cloning software to create identical test environments. This capability allows for safe testing of software updates, system changes, and new configurations without risking production systems.
Benefits for development and testing include:
- Consistent test environments across multiple machines
- Quick rollback capabilities if tests cause problems
- Isolation of test systems from production environments
- Ability to test various scenarios on identical system configurations
Common Issues and Troubleshooting
Cloning Failures
Insufficient Space One of the most common issues occurs when the destination drive lacks sufficient capacity for the clone. Always verify that the destination drive has adequate space, considering that sector-by-sector cloning requires space equal to the entire source drive capacity.
Hardware Conflicts Incompatible hardware can cause cloning failures. Ensure that all drives are properly connected and recognized by the system before starting the cloning process. Check cables, power connections, and drive health status.
Software Conflicts Running other disk-intensive applications during cloning can cause conflicts and failures. Close unnecessary programs and avoid heavy disk usage during the cloning process.
Boot Issues After Cloning
Boot Sector Problems If a cloned system won’t boot, the boot sector may not have been copied correctly. Many cloning software packages include boot repair utilities to fix these issues.
Drive Letter Conflicts Windows may assign different drive letters to cloned drives, potentially causing boot problems. Use disk management tools to assign appropriate drive letters before attempting to boot from the cloned drive.
Hardware Driver Issues When moving clones to different hardware, driver conflicts may prevent proper booting. Use universal restore features if available, or prepare to install appropriate drivers for the new hardware.
Performance Issues
Slow Cloning Speed Several factors can impact cloning speed:
- USB connection speeds (USB 2.0 vs. USB 3.0 vs. USB-C)
- Drive health and fragmentation
- System resource availability
- Software efficiency and algorithms
System Slowdown During Cloning Live cloning can impact system performance. Schedule cloning operations during low-usage periods or use bootable media for cloning to avoid system performance impacts.
Security Considerations
Data Encryption
When creating clones containing sensitive information, consider encryption options to protect data from unauthorized access. Many enterprise-grade cloning solutions offer built-in encryption capabilities.
Encryption considerations include:
- Algorithm strength (AES-256 is current standard)
- Key management and storage
- Performance impact of encryption
- Compliance requirements for regulated industries
Physical Security
Cloned drives contain complete copies of sensitive data and should be secured appropriately. Store backup drives in secure locations and consider the physical security implications of having multiple copies of critical data.
Access Control
Limit access to cloning software and cloned drives to authorized personnel only. In business environments, implement proper access controls and audit trails for cloning operations.
Advanced Cloning Techniques
Network-Based Cloning
Advanced cloning solutions support network-based operations, allowing clones to be created across network connections. This capability is valuable for:
- Remote system management
- Centralized backup operations
- Large-scale deployments
- Situations where physical access is limited
Differential and Incremental Cloning
Some advanced cloning software supports differential and incremental cloning techniques:
Differential Cloning: Only copies data that has changed since the last full clone, reducing time and storage requirements while maintaining complete system recoverability.
Incremental Cloning: Copies only data that has changed since the last clone operation (full or incremental), providing the most efficient use of storage and time.
Cloud-Based Cloning
Modern cloning solutions increasingly offer cloud integration, allowing clones to be stored in cloud storage services. This approach provides:
- Off-site backup capabilities
- Accessibility from multiple locations
- Scalable storage options
- Protection against local disasters
Industry Applications
Healthcare
Healthcare organizations use cloning software to maintain critical systems that store patient data and support medical equipment. The ability to quickly restore systems ensures continuity of care and compliance with healthcare regulations.
Education
Educational institutions rely on cloning software to manage computer labs and classroom systems. Standardized system images can be quickly deployed across multiple machines, ensuring consistent learning environments.
Financial Services
Financial institutions use cloning for disaster recovery and business continuity planning. The ability to quickly restore trading systems and customer service platforms is critical for maintaining operations and regulatory compliance.
Manufacturing
Manufacturing companies use cloning to maintain industrial control systems and manufacturing execution systems. Quick recovery capabilities minimize production downtime and associated costs.
Future Trends in Cloning Software
Cloud Integration
The future of cloning software involves deeper cloud integration, with hybrid solutions that combine local cloning speed with cloud-based storage and management capabilities.
AI-Powered Optimization
Artificial intelligence and machine learning algorithms are being integrated into cloning software to optimize cloning processes, predict potential issues, and recommend optimal cloning strategies.
Container and Virtual Machine Support
As virtualization and containerization become more prevalent, cloning software is evolving to better support these technologies, offering specialized cloning capabilities for virtual environments.
Enhanced Security Features
Future cloning solutions will include more sophisticated security features, including advanced encryption, secure key management, and integration with enterprise security frameworks.
Choosing the Right Cloning Software
Assessment Criteria
When selecting cloning software, consider:
Feature Requirements: Identify essential features such as live cloning, compression, encryption, and file system support based on your specific needs.
Ease of Use: Evaluate the user interface and documentation quality, especially if multiple users will operate the software.
Performance: Consider cloning speed, system resource usage, and efficiency for your typical use cases.
Support and Updates: Assess the vendor’s support quality, update frequency, and long-term product viability.
Cost: Balance feature requirements with budget constraints, considering both initial costs and ongoing maintenance expenses.
Trial and Evaluation
Most commercial cloning software offers trial versions or money-back guarantees. Take advantage of these opportunities to test software with your specific hardware and use cases before making a final decision.
Vendor Reputation
Research vendor reputation, customer reviews, and industry recognition. Established vendors with strong track records are more likely to provide reliable software and ongoing support.
Implementation Best Practices
Documentation
Maintain detailed documentation of your cloning procedures, including:
- Software configuration settings
- Hardware requirements and compatibility
- Step-by-step procedures
- Troubleshooting guides
- Recovery procedures
Testing and Validation
Regularly test your cloning procedures to ensure they work correctly when needed. Verify that cloned systems boot properly and that all critical applications function correctly.
Regular Updates
Keep cloning software updated to ensure compatibility with new operating systems, hardware, and security requirements. Subscribe to vendor notifications about updates and security patches.
Training
Ensure that all users who will operate cloning software receive appropriate training. Document procedures and provide hands-on practice opportunities to build confidence and competency.
Conclusion
Cloning software represents an essential tool for modern digital life, providing comprehensive protection against data loss and enabling efficient system management. Whether you’re a home user protecting personal files or an IT professional managing enterprise systems, understanding and implementing proper cloning solutions can save time, money, and stress when technology challenges arise.
The key to successful implementation lies in choosing appropriate software for your specific needs, following best practices for deployment and operation, and maintaining current knowledge of evolving technologies and techniques. As storage technologies continue to evolve and data volumes grow, cloning software will remain a critical component of comprehensive data protection and system management strategies.
By implementing robust cloning solutions today, you’re not just protecting your current digital assets â you’re building a foundation for resilient digital operations that can adapt and scale with your evolving needs. The investment in quality cloning software and proper procedures pays dividends through reduced downtime, faster recovery times, and the peace of mind that comes from knowing your digital life is properly protected.
Remember that cloning software is just one component of a comprehensive data protection strategy. Combine it with regular backups, security measures, and disaster recovery planning to create a robust defense against data loss and system failures. With proper planning and implementation, cloning software can transform from a reactive disaster recovery tool into a proactive system management solution that enhances efficiency and reliability across all your digital operations.







